The
IP Multimedia Subsystem (IMS) facilitates telecom operators in
delivering multimedia applications and voice traffic over IP transport. Proxy
Call Session Control Function (P-CSCF) is the first node in IMS Platform (figure
1) to interact with the User Equipment (UE) when initiating a VoLTE call.
 |
figure
1 - Placement of P-CSCF in IMS Platform
|
1) Initiate a call with VoLTE phone and simultaneously open phone's terminal to list currently established sessions. It was possible to identify the IP address of serving P-CSCF node, connected on port 5060 (figure 2).
 |
figure
2 - Identifying P-CSCF node connected on port 5060 (SIP protocol)
|
 |
figure
4 - Application server's management console
|
3)
Application server, Oracle Glassfish, was found to be weakly configured and
could be accessed using weak credentials (figure 5).
 |
figure
5 - Access to Oracle Glassfish server using weak credentials
|
4)
A reverse shell was triggered using a web shell and gained root access of the
P-CSCF node (figure 6).
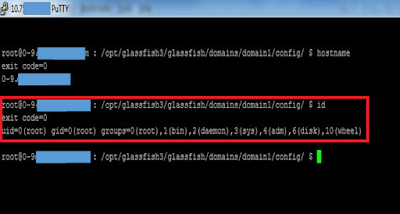 |
| figure 6 - Gained root access to P-CSCF (IMS) |
After gaining access to the IMS platform, Attacker can compromise other core telecom components in the network.
To prevent from such attacks, telecom operators should ensure traffic segregation between user plane, control plane and management plane. It is highly recommended to patch all the core network elements with latest security patches released by the vendor. Also develop and implement minimum security guidelines before integrating nodes in the network.
Hope
you enjoyed reading, suggestions are always welcome.
